Multi-Factor Authentication (MFA) Guide For A COVID Work-From-Anywhere World

If you don’t have Multi-Factor Authentication (MFA) set up for your Microsoft 365 email account (or any email account), you need to set it up – TODAY. Email based attacks have been on the rise as data thieves are adjusting to the COVID Work-From-Anywhere culture.
Even if you do currently use MFA – it’s time to make sure you are using it correctly.
What is Multi-Factor Authentication?
Don’t be frightened by its name, Multi-Factor Authentication (MFA) simply means that you are requiring more than one type of verification when you sign into a platform. Think of it like when you get a new job or apply for a passport, you have to show two forms of ID. MFA is like that.
Also like a new job, you don’t need to show two forms of ID every day you go to work. Once you’ve shown them, your workplace knows you and remembers you. MFA is the same. The first time you login to your Microsoft 365 email on your home computer, the MFA will be triggered. But it will then remember you. At least until you go on your vacation. Depending on how long you’ve been inactive on that device, you may need to authenticate again.
But not all Multi-Factor Authentication is the same. There are different methods of authentication, some of which are more secure than others. Here’s the rundown.
Multi-Factor Authentication By App
Authentication by app is the most secure method of MFA available. There are several apps you can use, the most common of which are:
- Microsoft Authenticator (App Store / Play)
- Google Authenticator (App Store / Play)
- Twilio Authy (App Store / Play)
- Duo (App Store / Play)
When using an authentication app, the user has the app installed on their smartphone. When logging into a platform (a computer or a mobile device), the Multi-Factor Authentication is triggered. The user goes to the app and gets a code that they manually enter into the MFA prompt on the platform they are trying to access. There is a different code for every platform they authenticate with the app.
MFA by app is the most secure because it requires both that the user physically has a device that belongs to them on their person and because they need to manually enter the authentication code to login.
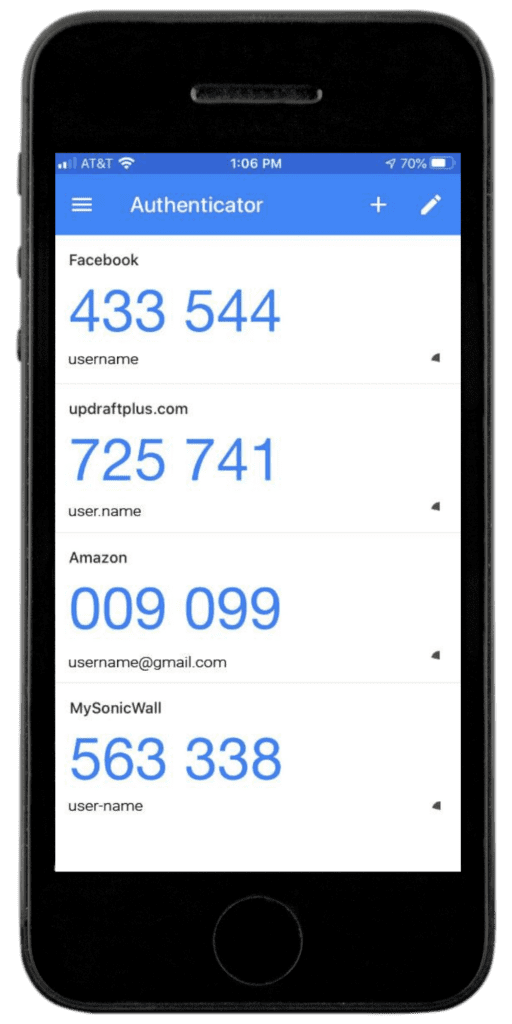
Multi-Factor Authentication By Text
Authentication by text is the next most secure method of MFA after the app. When logging into a platform that triggers MFA, a code is texted to the user. The user gets the code from the text message and manually enters it into the MFA prompt on the platform. The code is tied to the user’s phone number, which is what makes this less secure than the app method.
Phone numbers are at risk of SIM jacking. That’s when a bad actor uses personal information they’ve gathered on you (often through social media) to convince your cell phone company that they are you. Then they transfer your SIM to another device and have access to any codes generated by MFA text.
SIM jacking, also called SIM swapping or SIM hijacking, is not the most common type of data theft, but it is on the rise. Given the relative ease of an authentication app, you are better off using the app.
Multi-Factor Authentication By Token Device
Some people, even in 2020, do not have smartphones. Or they do, but aren’t allowed to have them in certain settings. Manufacturing and financial workers, for example, may not be allowed to have smartphones at work.
In this case, the most secure method of authentication is using a hardware token device, such as Yubikey. These look similar to a key fob and need to be configured to receive authentication. But when needed, you can use the code that appears on the device to authenticate your login.
Authentication Methods That We Don’t Recommend (BLOCK)
There are ways to authenticate that we don’t recommend. In fact, we actually block these when rolling out Microsoft 365 Multi-Factor Authentication for our customers.
- MFA by Alternate Email
Email is actually compromised far more often than phones and SIM cards. And often it’s not just one email account that gets hacked, it’s multiple. So there is too high a chance that a hacker would intercept authentication to an alternate email. - MFA by Push Notification
The problem with push notifications is how much they vary. Some require multiple clicks to accept and verify, while others are a simple pop-up on top of the phone screen with a single prompt to approve. Not only is it easy to click it by accident, but it’s also hard to know what you are approving. We’ve actually seen clients approve access by push notification thinking it was one of their devices trying to connect when they were really letting a hacker into their account. - MFA by Phone Call
Like the push notification, MFA by phone call has a lot of variations. Some simply require you to say “yes” or push # to verify with little or no other information required. And as with push notifications, we’ve seen clients allow hackers into their accounts with MFA by phone call.
5 Steps To Better Multi-Factor Authentication
There is no magic bullet for complete security. But, Multi-Factor Authentication is, hands down, the BEST method available to prevent unauthorized account access IF it is configured properly.
Here are some steps to making your MFA better:
- Set up Multi-Factor Authentication – YESTERDAY – across all your business email accounts. For employers, require your employees to do the same.
- Take a look at all your vendors and partners (e.g., banking, insurance, payroll, 401k). Do they offer MFA? If not, it’s time to find a new provider that does.
- Set up MFA across all your business vendor and partner accounts, preferably using the authenticator app method.
- Set up MFA for your personal banking, investment, insurance and health-related accounts to ensure your identity is protected.
- Monitor access attempts. For personal accounts, this can mean turning on notifications that tell you when an account is being accessed from any new devices. For companies, the principle is the same, but you’ll need an IT team or partner to help.
Real-Time Monitoring For Your Business
Businesses need sophisticated monitoring that takes into account multiple data points. For instance, a basic alert will tell you that a user is trying to login from a new location for the first time. More sophisticated monitoring takes into account the last time the user logged in and the distance between the two locations. For instance, someone logs in from Cincinnati and then 20 minutes later there’s a login attempt from Turkey. There’s no way a person could get from Cincinnati to Turkey in 20 minutes, so there’s definitely a malicious act involved. Depending on the business, we can set up your system to block all international sign ins.
Monitoring is even more critical in the new COVID-19 work-from-anywhere culture. At Intrust-IT, we monitor all of our CompleteCare clients. When login attempts occur, we check if it was successful or unsuccessful, as well as whether any MFA criteria were met for the sign in. If something suspicious is found, a member of our engineering team who specializes in cybersecurity evaluates it immediately. If we’re unable to contact the account owner or company representative where the login occurred, we can temporarily disable the account.
In just the last week, we prevented two accounts from being compromised through monitoring and were able to stop attempted hacks on two others before significant damage could be done. In three of the four cases, the users had not yet implemented their Multi-Factor Authentication.
The Time For MFA Is Now Yesterday
The days of someone hacking a company network to steal data or hold it for ransom are more and more in our rear view mirror. It still happens, but not nearly as often – in part because of new end-point protection and network perimeter security systems that effectively block those attempts, making it much more costly and time consuming to try and accomplish.
The types of breaches that are becoming more common are those that exploit individual accounts. Data thieves use social engineering tactics like well-crafted phishing emails. Once in your account, they steal what they can, then branch out using your contacts to snare more people. The best defense against this growing threat is a well-configured Multi-Factor Authentication program.
Watch each video and make simple, everyday changes that will help reduce your risks of hacks, breaches and cyber attacks.

P is for Passwords
5 things you can do today to keep your company safe

I is for Insurance and Investments
3 easy things you can do to reduce your risk

E is for Employees
4 ways employees can keep your company safe Get Free Access
Share this Blog

Is Your Name or Birthday a Part of Your Password?
If so, you’re a part of the 59 percent of people who don’t follow proper password hygiene. More than 70 percent of passwords are used for more than one system, meaning if cybercriminals crack one, they can access a lot more accounts.
Our free Enterprise Password Management Guide will give you the best password hygiene practices to help you secure your computer and your business.
Download the Guide
Explore the Latest Trends in IT

Securing Our Cities: Cybersecurity Protection for Local Governments

Manufacturing and IoT: Securing Connected Devices

Small Business Cyber Security Toolkit: The Tools You Need to Stay Protected




